We have all used login forms on many websites. But have you ever thought what is the need for login forms? Login methods keep the data safe for the user. One user can only access a desired amount of information. With the help of authentication, we can limit the functionality of the user and verify each piece of information on the database with a unique key. From this information, we can classify the data that can later be used for analysis.
To make all these work in an efficient manner we need to have some kind of authentification system. That will verify all the requests made by the user, format data based on the user ID, and secure the database. This is the place where JWT comes into the picture. so what is JWT?
JWT
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed.
In simple terms, it is a keyword that we first get from the backend server, which we later send with each request. The server verifies this keyword and executes the request if it passes else it rejects the request and sends a 404 unauthorized code.
Inside JWT
Inside JWT there are three things header, payload, and signature. Which are separated by dots and can be identified by their positions header.payload.signature
Header - The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA.
{ "typ": "JWT", "alg": "HS256" }Payload - The payload contains claims, which are statements about an entity (typically, the user) and additional data. There are three types of claims: registered, public, and private claims
{ "sub": "user10001", "iat": 1569302116 }Signature - The signature is most important part of a JSON Web Token(JWT). The signature is used to verify that the sender of the JWT is who it claims to be and to ensure that the message wasn't changed along the way.
Working of JWT
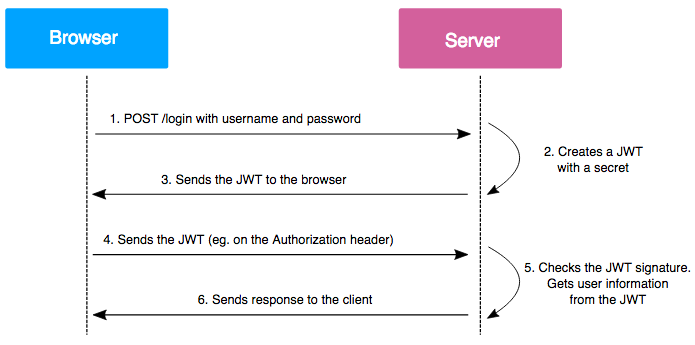
Users sign in using a username and password or use any Auth service.
The authentication server verifies the credentials and issues a JWT.
JWT can be signed using a secret (HMAC) or a public/private key pair using RSA or ECDSA.
Once the recipient has the JWT, they can check the signature and use the information stored in the payload, such as user ID and role, to authorize the request.
JWTs are often used as authentication tokens, allowing the user to authenticate once and then make requests to the server without sending their credentials with each request.
How secure is JWT?
The security of JSON Web Tokens (JWT) depends on several factors:
Cryptographic algorithms: The security of the JWT depends on the strength of the signing algorithm used to sign the token. For example, HMAC with SHA-256 is considered secure, while HS256 with SHA-1 is not.
Token expiration: JWTs should have a limited lifetime to reduce the risk of token replay attacks. A token replay attack occurs when an attacker intercepts a JWT and uses it again to gain unauthorized access to a system.
Secret key management: If a JWT is signed using a secret key (HMAC), it's important to keep the secret key secure. If the secret key is compromised, an attacker could generate their own JWTs and impersonate other users.
Payload content: The payload of a JWT should only contain information that is necessary for the application. Avoid including sensitive information, such as passwords, in the payload.

